Little Snitch Is A Vpn
By now, any sentient IT person knows the perils of open Wi-Fi. Those free connections in cafes and hotels don't encrypt network traffic, so others on the network can read your traffic and possibly hijack your sessions. But one of the main solutions to this problem has a hole in it that isn't widely appreciated.
Few people are Little Snitch Vpn aware that public WiFi is insecure; information such as internet banking passwords are easy for fraudsters to access when using public networks. Therefore, a VPN is essential. Aug 16, 2015 When a VPN connection is established, the Mac sees this as a new “network” called “OpenVPN”, which can therefore be used to trigger a “Trusted” profile in Little Snitch, once again allowing all my desired incoming and outgoing traffic.
Large sites like Twitter and Google have adopted SSL broadly in order to protect users on such networks. But for broader protection, many people use a virtual private network (VPN). Most people, if they use a VPN at all, use a corporate one. But there are public services as well, such as F-Secure's Freedome and Privax's HideMyAss. Your device connects with the VPN service's servers and establishes an encrypted tunnel for all your Internet traffic from the device to their servers. The service then proxies all your traffic to and from its destination.
It's a better solution than relying on SSL from websites for a number of reasons: with a VPN, all of the traffic from your device is encrypted, whether the site you are visiting has SSL or not. Even if the Wi-Fi access point to which you are connected is malicious, it can't see the traffic. Any party that is in a position to monitor your traffic can't even see the addresses and URLs of the sites with which you are communicating, something they can do with SSL over open Wi-Fi.
But there is a hole in this protection, and it happens at connect time. The VPN cannot connect until you connect to the Internet, but the VPN connection is not instantaneous. In many, perhaps most public Wi-Fi sites, your Wi-Fi hardware may connect automatically to the network, but you must open a browser to a 'captive portal,' which comes from the local router, and attempt to gain access to the Internet beyond. You may have to manually accept a TOS (Terms of Service) agreement first.
In this period before your VPN takes over, what might be exposed depends on what software you run. Do you use a POP3 or IMAP e-mail client? If they check automatically, that traffic is out in the clear for all to see, including potentially the login credentials. Other programs, like instant messaging client, may try to log on.
I tested this scenario at a Starbucks with Google Wi-Fi while running Wireshark. Thousands of packets went back and forth on the open network before the VPN attempted to connect. A quick scan of the list found nothing that looked dangerous, and in fact the software on my system used TLS 1.2 in almost all cases, which was quite a relief. But your configuration may be different from mine, and even if your software attempts to use HTTPS, it could be vulnerable to attacks like SSLStrip, which tricks the software into using open HTTP anyway.
This gap in coverage may only be a matter of seconds, but that's enough to expose valuable information like logon credentials. Try running a network monitoring tool like Microsoft's TCPView for Windows or Little Snitch for Mac before you establish your Internet connection and see what happens in those first few seconds. The information may be protected by encryption, but it can carry details about your system configuration that could be used to identify it—or provide clues for an attacker.
Even beyond this time gap, sometimes VPN connections go down. At least in the default configurations of most operating systems, the applications on the system will fail over to the open Wi-Fi connection. Don't blame just the public VPN vendors. The same problem is true of corporate VPNs, unless they go to the trouble of configuring the system around the problem.
So, how do you do that? Shaun Murphy, a founder of PrivateGiant (www.privategiant.com), which makes products to protect the security and privacy of online communications, suggests that you do it with a software firewall, either one that comes with your operating system or a third-party one:
The basic approach is to prevent all inbound and outbound connections on your public networks (or zones) with the exception of a browser that you use to connect to captive portals and such. That browser should be one you only use for this purpose and, perhaps, some lightweight browsing (certainly not email, social, or any other personally identifiable purpose.) Using that same firewall, set up a profile/zone for VPN traffic where inbound / outbound traffic are less restricted (I recommend blocking outbound connections by default and then adding in programs as needed, it's surprising how many programs call home.. all the time.) The nice thing about this approach is your email client, primary web browser, and other applications you use will be useless unless you are actively connected to the VPN.
Sean Sullivan, security advisor at F-Secure, gave us the same advice with the useful addition that '..you'd want to launch the browser [for the captive portal] in 'safe mode' so the plugins are disabled.' If you're a Firefox or Google Chrome user, then Internet Explorer and Safari should fit the bill. You've got them on the system anyway.
Configuring firewall software on your PC to block non-VPN traffic isn't all that easy. It varies across operating systems and products, and it may not even be possible in Windows 8.1. On Windows, here's a summary of what you'd need to do:
- Connect to the VPN of your choice using the normal procedure for that product.
- In the Network and Sharing Center in Control Panel, make sure the VPN connection is set as a Public network, and the home or public Wi-Fi network is set as Home or Office (Home is better). (In Windows 8 and later this can be problematic unless the network connection is brand new, because Windows 8.x provides no user interface with which to change the location type—so the whole exercise may be impossible—unless you first delete and recreate all your network connections.)
- Finally, in the Windows Firewall in Control Panel go to the Advanced Settings. Create a rule to block all programs from connecting on Public networks. Then create a rule to allow both the VPN program and the browser you want to use for the captive portal to be allowed to connect on Public networks. You will need to set these rules both for inbound and outbound connections.
BolehVPN of Hong Kong has produced a more detailed set of instructions for using the Windows Firewall in Windows 7. On a Mac, you can achieve the same results with the aforementioned Little Snitch firewall. And Douglas Crawford at BestVPN.com has instructions for the Comodo Firewall on Windows, but says that he couldn't get the procedure to work on the standard Windows Firewall in Windows 8.1.
All in all, it's a fair amount of trouble to go through, and it's a configuration you'd only want on open Wi-Fi. If you work where there is secure WPA2 encryption on the Wi-Fi, then the VPN is probably not worth the overhead and the reduced network performance.
The real solution to this problem isn't hacking with firewalls, it's providing encryption by default in public Wi-Fi. This isn't done much now because that would mean supplying passwords, and the support overhead would just be too great for a cafe. The result is that we have an insecure situation with bad, but adequate, usability.
The Wi-Fi Alliance has had a solution for this problem nearly in place for years, called Passpoint. The Passpoint protocol was created to allow for Wi-Fi 'roaming' by creating a way for access points to grant access by way of a third-party credential, such as your Google ID or your ISP account. When you connect to a public access point through Passpoint, it authenticates you and establishes a secure connection using WPA2-Enterprise, the gold standard in Wi-Fi security—instead of leaving your traffic unencrypted or visible on the shared wireless LAN.
The reason that you don't yet see Passpoint everywhere is that it requires the Wi-Fi provider—such as a consumer ISP, Google, or Boingo—to trust certain authentication providers and to advertise a list of them to connecting devices—the longer, the better. And users would need to configure Passpoint on their system to use one or more of their credentials when connecting to such a network. There hasn't been wide adoption of Passpoint yet—while it's been put to use in certain high-volume locations, such as many airports, it's still pretty uncommon.
The Wi-Fi Alliance now says that Passpoint is gaining traction in the enterprise as a way to handle BYOD. That's interesting if true, but it doesn't address the pain point of public Wi-Fi privacy. Passpoint has the potential to close the VPN data leakage window and make public Internet services far more secure. In its absence, there is no good solution.
First of all, check this and ensure that you are deploying to the supported ubuntu version.
- Installation Problems
- Connection Problems
Installation Problems
Look here if you have a problem running the installer to set up a new Algo server.
Python version is not supported
The minimum Python version required to run Algo is 3.6. Most modern operation systems should have it by default, but if the OS you are using doesn’t meet the requirements, you have to upgrade. See the official documentation for your OS, or manual download it from https://www.python.org/downloads/. Otherwise, you may deploy from docker
Error: “You have not agreed to the Xcode license agreements”
On macOS, you tried to install the dependencies with pip and encountered the following error:
The Xcode compiler is installed but requires you to accept its license agreement prior to using it. Run xcodebuild -license to agree and then retry installing the dependencies.
Error: checking whether the C compiler works… no
On macOS, you tried to install the dependencies with pip and encountered the following error:
You don’t have a working compiler installed. You should install the XCode compiler by opening your terminal and running xcode-select --install.
Error: “fatal error: ‘openssl/opensslv.h’ file not found”
On macOS, you tried to install cryptography and encountered the following error:
You are running an old version of pip that cannot download the binary cryptography dependency. Upgrade to a new version of pip by running sudo python3 -m pip install -U pip.
Error: “ansible-playbook: command not found”
You tried to install Algo and you see an error that reads “ansible-playbook: command not found.”
You did not finish step 4 in the installation instructions, “Install Algo’s remaining dependencies.” Algo depends on Ansible, an automation framework, and this error indicates that you do not have Ansible installed. Ansible is installed by pip when you run python3 -m pip install -r requirements.txt. You must complete the installation instructions to run the Algo server deployment process.
Fatal: “Failed to validate the SSL certificate”
You received a message like this:
Your local system does not have a CA certificate that can validate the cloud provider’s API. Are you using MacPorts instead of Homebrew? The MacPorts openssl installation does not include a CA certificate, but you can fix this by installing the curl-ca-bundle port with port install curl-ca-bundle. That should do the trick.
Could not fetch URL … TLSV1_ALERT_PROTOCOL_VERSION
You tried to install Algo and you received an error like this one:
It’s time to upgrade your python.
brew upgrade python3
You can also download python 3.7.x from python.org.
Bad owner or permissions on .ssh
You tried to run Algo and it quickly exits with an error about a bad owner or permissions:
You need to reset the permissions on your .ssh directory. Run chmod 700 /home/user/.ssh and then chmod 600 /home/user/.ssh/config. You may need to repeat this for other files mentioned in the error message.
The region you want is not available
Algo downloads the regions from the supported cloud providers (other than Microsoft Azure) listed in the first menu using APIs. If the region you want isn’t available, the cloud provider has probably taken it offline for some reason. You should investigate further with your cloud provider.
If there’s a specific region you want to install to in Microsoft Azure that isn’t available, you should file an issue, give us information about what region is missing, and we’ll add it.
AWS: SSH permission denied with an ECDSA key
You tried to deploy Algo to AWS and you received an error like this one:
Virtual guitarist vst plugin free download. 5 / 5I got the error installing the Visual C redistributable as well, but it does not stop the completion of the main installation. Full-velocity notes are meant to trigger a 'pop' sound, but you can get some really nice, smooth sounds by dialing it back a bit.Oct 23 2018. The download from the manufacturer's website had a trojan in it too that disabled by computer, so I had to do a system restore and deleted the Ample Sound plugin anyway, because it was so bad.dsntJan 30 2019If the pick attack sounds too harsh, turn down the note velocity.
You previously deployed Algo to a hosting provider other than AWS, and Algo created an ECDSA keypair at that time. You are now deploying to AWS which does not support ECDSA keys via their API. As a result, the deploy has failed.
In order to fix this issue, delete the algo.pem and algo.pem.pub keys from your configs directory and run the deploy again. If AWS is selected, Algo will now generate new RSA ssh keys which are compatible with the AWS API.
AWS: “Deploy the template fails” with CREATE_FAILED
Little Snitch Sale
You tried to deploy Algo to AWS and you received an error like this one:
Algo builds a Cloudformation template to deploy to AWS. You can find the entire contents of the Cloudformation template in configs/algo.yml. In order to troubleshoot this issue, login to the AWS console, go to the Cloudformation service, find the failed deployment, click the events tab, and find the corresponding “CREATE_FAILED” events. Note that all AWS resources created by Algo are tagged with Environment => Algo for easy identification.
In many cases, failed deployments are the result of service limits being reached, such as “CREATE_FAILED AWS::EC2::VPC VPC The maximum number of VPCs has been reached.” In these cases, you must either delete the VPCs from previous deployments, or contact AWS support to increase the limits on your account.
AWS: not authorized to perform: cloudformation:UpdateStack
You tried to deploy Algo to AWS and you received an error like this one:
This error indicates you already have Algo deployed to Cloudformation. Need to delete it first, then re-deploy.
DigitalOcean: error tagging resource
You tried to deploy Algo to DigitalOcean and you received an error like this one:
The error is caused because Digital Ocean changed its API to treat the tag argument as a string instead of a number.
- Download doctl
- Run
doctl auth init; it will ask you for your token which you can get (or generate) on the API tab at DigitalOcean - Once you are authorized on DO, you can run
doctl compute tag listto see the list of tags - Run
doctl compute tag delete environment:algo --forceto delete the environment:algo tag - Finally run
doctl compute tag listto make sure that the tag has been deleted - Run algo as directed
Windows: The value of parameter linuxConfiguration.ssh.publicKeys.keyData is invalid
You tried to deploy Algo from Windows and you received an error like this one:
This is related to the chmod issue inside /mnt directory which is NTFS. The fix is to place Algo outside of /mnt directory.
Docker: Failed to connect to the host via ssh
You tried to deploy Algo from Docker and you received an error like this one:
You need to add the following to the ansible.cfg in repo root:
Wireguard: Unable to find ‘configs/…’ in expected paths
You tried to run Algo and you received an error like this one:
This error is usually hit when using the local install option on a server that isn’t Ubuntu 18.04. You should upgrade your server to Ubuntu 18.04. If this doesn’t work, try removing *.lock files at /etc/wireguard/ as follows:
Then immediately re-run ./algo.
Ubuntu Error: “unable to write ‘random state’” when generating CA password
When running Algo, you received an error like this:
This happens when your user does not have ownership of the $HOME/.rnd file, which is a seed for randomization. To fix this issue, give your user ownership of the file with this command:
Now, run Algo again.
Connection Problems
Look here if you deployed an Algo server but now have a problem connecting to it with a client.
I’m blocked or get CAPTCHAs when I access certain websites
Little Snitch Mac
This is normal.
When you deploy a Algo to a new cloud server, the address you are given may have been used before. In some cases, a malicious individual may have attacked others with that address and had it added to “IP reputation” feeds or simply a blacklist. In order to regain the trust for that address, you may be asked to enter CAPTCHAs to prove that you are a human, and not a Denial of Service (DoS) bot trying to attack others. This happens most frequently with Google. You can try entering the CAPTCHAs or you can try redeploying your Algo server to a new IP to resolve this issue.
In some cases, a website will block any visitors accessing their site through a cloud hosting provider due to previous, frequent DoS attacks originating from them. In these cases, there is not much you can do except deploy Algo to your own server or another IP that the website has not outright blocked.
I want to change the list of trusted Wifi networks on my Apple device
This setting is enforced on your client device via the Apple profile you put on it. You can edit the profile with new settings, then load it on your device to change the settings. You can use the Apple Configurator to edit and resave the profile. Advanced users can edit the file directly in a text editor. Use the Configuration Profile Reference for information about the file format and other available options. If you’re not comfortable editing the profile, you can also simply redeploy a new Algo server with different settings to receive a new auto-generated profile.
Error: “The VPN Service payload could not be installed.”
You tried to install the Apple profile on one of your devices and you received an error stating The 'VPN Service' payload could not be installed. The VPN service could not be created. Client support for Algo VPN is limited to modern operating systems, e.g. macOS 10.11+, iOS 9+. Please upgrade your operating system and try again.
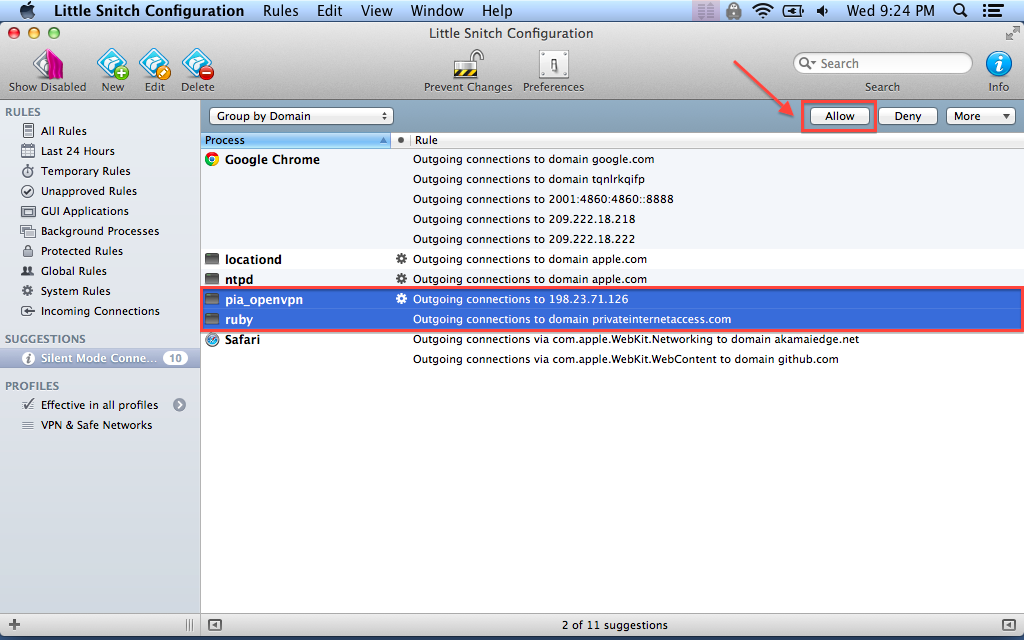
Little Snitch is broken when connected to the VPN
Little Snitch is not compatible with IPSEC VPNs due to a known bug in macOS and there is no solution. The Little Snitch “filter” does not get incoming packets from IPSEC VPNs and, therefore, cannot evaluate any rules over them. Their developers have filed a bug report with Apple but there has been no response. There is nothing they or Algo can do to resolve this problem on their own. You can read more about this problem in issue #134.
I can’t get my router to connect to the Algo server
In order to connect to the Algo VPN server, your router must support IKEv2, ECC certificate-based authentication, and the cipher suite we use. See the ipsec.conf files we generate in the config folder for more information. Note that we do not officially support routers as clients for Algo VPN at this time, though patches and documentation for them are welcome (for example, see open issues for Ubiquiti and pfSense).
I can’t get Network Manager to connect to the Algo server
You’re trying to connect Ubuntu or Debian to the Algo server through the Network Manager GUI but it’s not working. Many versions of Ubuntu and some older versions of Debian bundle a broken version of Network Manager without support for modern standards or the strongSwan server. You must upgrade to Ubuntu 17.04 or Debian 9 Stretch, each of which contain the required minimum version of Network Manager.
Various websites appear to be offline through the VPN
This issue appears occasionally due to issues with MTU size. Different networks may require the MTU to be within a specific range to correctly pass traffic. We made an effort to set the MTU to the most conservative, most compatible size by default but problems may still occur.
If either your Internet service provider or your chosen cloud service provider use an MTU smaller than the normal value of 1500 you can use the reduce_mtu option in the file config.cfg to correspondingly reduce the size of the VPN tunnels created by Algo. Algo will attempt to automatically set reduce_mtu based on the MTU found on the server at the time of deployment, but it cannot detect if the MTU is smaller on the client side of the connection.
If you change reduce_mtu you’ll need to deploy a new Algo VPN.
To determine the value for reduce_mtu you should examine the MTU on your Algo VPN server’s primary network interface (see below). You might algo want to run tests using ping, both on a local client when not connected to the VPN and also on your Algo VPN server (see below). Then take the smallest MTU you find (local or server side), subtract it from 1500, and use that for reduce_mtu. An exception to this is if you find the smallest MTU is your local MTU at 1492, typical for PPPoE connections, then no MTU reduction should be necessary.
Check the MTU on the Algo VPN server
To check the MTU on your server, SSH in to it, run the command ifconfig, and look for the MTU of the main network interface. For example:
The MTU shown here is 1460 instead of 1500. Therefore set reduce_mtu: 40 in config.cfg. Algo should do this automatically.
Determine the MTU using ping
When using ping you increase the payload size with the “Don’t Fragment” option set until it fails. The largest payload size that works, plus the ping overhead of 28, is the MTU of the connection.
Example: Test on your Algo VPN server (Ubuntu)
In this example the largest payload size that works is 1432. The ping overhead is 28 so the MTU is 1432 + 28 = 1460, which is 40 lower than the normal MTU of 1500. Therefore set reduce_mtu: 40 in config.cfg.
Example: Test on a macOS client not connected to your Algo VPN
In this example the largest payload size that works is 1464. The ping overhead is 28 so the MTU is 1464 + 28 = 1492, which is typical for a PPPoE Internet connection and does not require an MTU adjustment. Therefore use the default of reduce_mtu: 0 in config.cfg.
Change the client MTU without redeploying the Algo VPN
If you don’t wish to deploy a new Algo VPN (which is required to incorporate a change to reduce_mtu) you can change the client side MTU of WireGuard clients and Linux IPsec clients without needing to make changes to your Algo VPN.
For WireGuard on Linux, or macOS (when installed with brew), you can specify the MTU yourself in the client configuration file (typically wg0.conf). Refer to the documentation (see man wg-quick).
For WireGuard on iOS and Android you can change the MTU in the app.
For IPsec on Linux you can change the MTU of your network interface to match the required MTU. For example:
To make the change take affect after a reboot, on Ubuntu 18.04 and later edit the relevant file in the /etc/netplan directory (see man netplan).
Note for WireGuard iOS users
As of WireGuard for iOS 0.0.20190107 the default MTU is 1280, a conservative value intended to allow mobile devices to continue to work as they switch between different networks which might have smaller than normal MTUs. In order to use this default MTU review the configuration in the WireGuard app and remove any value for MTU that might have been added automatically by Algo.
Clients appear stuck in a reconnection loop
If you’re using ‘Connect on Demand’ on iOS and your client device appears stuck in a reconnection loop after switching from WiFi to LTE or vice versa, you may want to try disabling DoS protection in strongSwan.
The configuration value can be found in /etc/strongswan.d/charon.conf. After making the change you must reload or restart ipsec.
Example command:
WireGuard: Clients can connect on Wifi but not LTE
Certain cloud providers (like AWS Lightsail) don’t assign an IPv6 address to your server, but certain cellular carriers (e.g. T-Mobile in the United States, EE in the United Kingdom) operate an IPv6-only network. This somehow leads to the Wireguard app not being able to make a connection when transitioning to cell service. Go to the Wireguard app on the device when you’re having problems with cell connectivity and select “Export log file” or similar option. If you see a long string of error messages like “Failed to send data packet write udp6 [::]:49727->[2607:7700:0:2a:0:1:354:40ae]:51820: sendto: no route to host then you might be having this problem.
Manually disconnecting and then reconnecting should restore your connection. To solve this, you need to either “force IPv4 connection” if available on your phone, or install an IPv4 APN, which might be available from your carrier tech support. T-mobile’s is available for iOS here under “iOS IPv4/IPv6 fix”, and here is a walkthrough for Android phones.
IPsec: Difficulty connecting through router
Some routers treat IPsec connections specially because older versions of IPsec did not work properly through NAT. If you’re having problems connecting to your AlgoVPN through a specific router using IPsec you might need to change some settings on the router.
Change the “VPN Passthrough” settings
If your router has a setting called something like “VPN Passthrough” or “IPsec Passthrough” try changing the setting to a different value.
Change the default pfSense NAT rules
If your router runs pfSense and a single IPsec client can connect but you have issues when using multiple clients, you’ll need to change the Outbound NAT mode to Manual Outbound NAT and disable the rule that specifies Static Port for IKE (UDP port 500). See Outbound NAT in the pfSense Book.
I have a problem not covered here

If you have an issue that you cannot solve with the guidance here, join our Gitter and ask for help. If you think you found a new issue in Algo, file an issue.